Chinese state-sponsored cyber actors were observed using the 7-Zip utility to unzip imported tools and malware files onto the victim device. Spearphishing personnel to deliver malicious payloads including ransomware.

Ttps Within Cyber Threat Intelligence Optiv
The same threat and risk assessment and analysis process can be applied to cyber-security.

Do threat actors procedures. Threat intelligence is important for the following reasons. The Cyber-security Threat and Risk Assessment. We care about these phishing incidents because once a hacker obtains credentials there is nothing to stand in the way of the threat actor.
Advanced Persistent Threat actors often use a careful and measured process to their efforts to secure access information or other gain. Which type of threat actor do these steps guard against. For example Initial Access is a tactic a threat actor would leverage to gain a foothold into your network.
The IT manager in your organization proposes taking steps to deflect a potential threat actor. What you can do. The word Tactics is meant to outline the way an adversary chooses to.
Analysis of TTPs aids in counterintelligence and security operations by describing how threat actors perform attacks. The 10 most dangerous cyber threat actors. In at least one case APT27 actors used a compromised account at one victim organization to send a spear phishing email.
To further break down TTP Tactics refer to the high-level descriptions of the behavior or action the threat actor is trying to accomplish. The proposal includes the following. Create and follow onboarding and off-boarding procedures.
THREAT IDENTIFICATION AND RATING OVERVIEW The first step in the assessment process is to help you to identify threats that are a priority concern in your area and that may pose a risk to your assets see Figure 1-1. Cyber threat actor tactics techniques and procedures TTPs DDoS. Sheds light on the unknown enabling security teams to make better decisions.
Of your customers networks eg the internet at your offices software eg your customer management system and hardware the laptops and desktops. Top threats facing an organization should be given priority for TTP maturation. Threat Actor Technique Sub-Techniques Threat Actor Procedures Detection and Mitigation Recommendations Defensive Tactics and Techniques.
Tactics Techniques and Procedures. Threat Overview Tactics Techniques and Procedures. So who cares if someone got the email login creds for Jeff from Accounting or Admin privileges to the printer on Floor 6 you might ask.
A distributed denial of service DDoS attack is a malicious attempt to disrupt the normal traffic of a targeted. Tactics techniques and procedures TTPs are the patterns of activities or methods associated with a specific threat actor or group of threat actors. A cyber-security threat risk assessment can involve protecting information eg the PII.
In recent years the groups tactics techniques and procedures have changed to integrate ransomware something that. As the report says insider threats are influenced by a combination of technical behavioral and organizational issues and must be addressed by policies procedures and technologies. Advanced threat actors will adapt their approaches and tools based on their effectiveness against a target.
Chinese state-sponsored cyber actors Reconnaissance TTPs with detection and mitigation recommendations Threat Actor Technique Sub-Techniques Threat Actor Procedures Detection and Mitigation Recommendations Defensive Tactics and Techniques Active Scanning T1595 Chinese state-sponsored cyber actors have been assessed to perform. Empowers cyber security stakeholders by revealing adversarial motives and their tactics techniques and procedures TTPs helps security professionals better understand the threat actors decision-making process. The threat identification and rating process involves the fol-.
Tactics Techniques and Procedures TTP Executed after the Breach. WWS facilities may be vulnerable to the following common tactics techniques and procedures TTPs used by threat actors to compromise IT and OT networks systems and devices. Malware refers to software that is purposefully designed in.
Integrate Threat Reputation Services Leverage multi-sourced threat reputation services for files DNS URLs IPs and email addresses. APT27 threat actors are not known for using original zero-day exploits but they may leverage those exploits once they have been made public. Threat actors hide malicious actions and remove data over common protocols making the need for sophisticated application-aware defensive mechanisms critical for modern network defenses.
DeobfuscateDecode Files or Information. In a similar fashion insiders are a threat to any organization since they already have some level of access to the information systems. Defining Tactics Techniques and Procedures.
Conversely nation-state actors conduct more targeted operations against organizations they want to exploit for espionage purposes or to gain leverage over. In addition APT actors may adapt and customize their Tactics Techniques and Procedures TTP to. THREAT IDENTIFICATION AND RATING 1-1 STEP 1.
Have appropriate physical security controls in place. The term Tactics Techniques and Procedures TTP describes an approach of analyzing an APTs operation or can be used as means of profiling a certain threat actor. TTPs Within Cyber Threat Intelligence.
Employ the principal of least privilege.

Comprehensive Threat Intelligence Recent Muddywater Associated Blackwater Campaign Shows Signs Of New Anti Detection Techniques
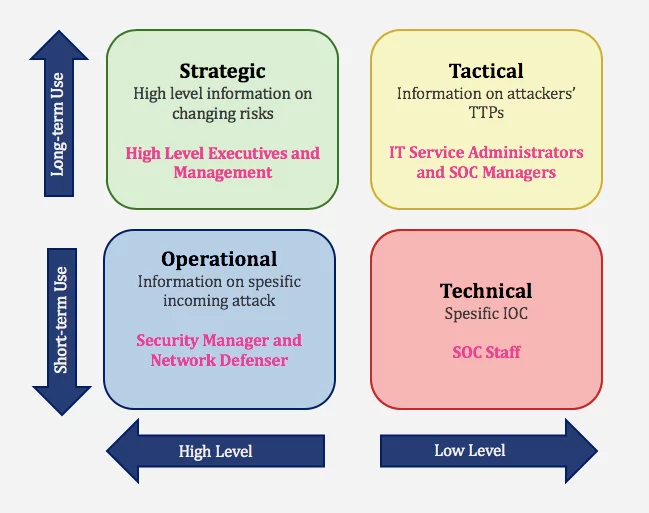
What Is Tactical Cyber Threat Intelligence And How To Use It Socradar Cyber Intelligence Inc

Election Security Spotlight Cyber Threat Actors

Distribute Threat Intelligence Overview Info Savvy Cyber Threat Threat Cyber

Security Verification Services Cyber Security Security Digital

Autottp Automated Tactics Techniques Procedures Techniques Cyber Security Infiltration

Tactics Techniques And Procedures Ttps Within Cyber Threat Intelligence Cyber Threat Cyber Threat Intelligence Threat

School Threat Assessment Template New Example Of A Location Risk Assessment Sheet Risk Management Safety Management System Risk Analysis

Cyber Threat And Cyber Threat Actors Canadian Centre For Cyber Security